
Claroty Secure Remote Access (SRA)
Claroty SRA delivers frictionless, reliable, and highly secure remote access to industrial and government environments for internal and third-party users.

Claroty SRA delivers frictionless, reliable, and highly secure remote access to industrial and government environments for internal and third-party users.
Unlike traditional remote access solutions—most of which are designed for IT networks—Claroty SRA is purpose-built for the specific operational, administrative, and security needs of industrial and government networks.
SRA removes the complexity and administrative barriers to effective, efficient remote access to environments for both internal and third-party users.
Remote access is the most commonly exploited attack vector for industrial and government environments. SRA eliminates this with a secure architecture and granular access controls.
All SRA user sessions enable live, over-the-shoulder monitoring, live disconnects if needed, and full-length recordings to support audit requests and investigations.
SRA’s purpose-built user experience makes connecting, troubleshooting, and repairing assets fast and easy, no matter where assets or users are located.
No jump servers here. Whether an internal engineer or third-party vendor, SRA enables all approved users to gain access quickly and painlessly through an intuitive interface that mimics their on-premise workstation. SRA also offers highly secure, controlled, safe access no matter where users, facilities, or assets are located.
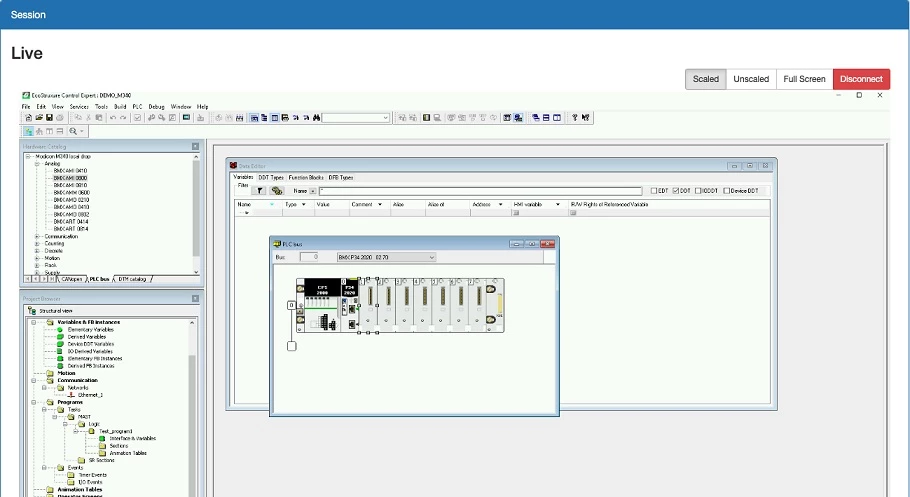
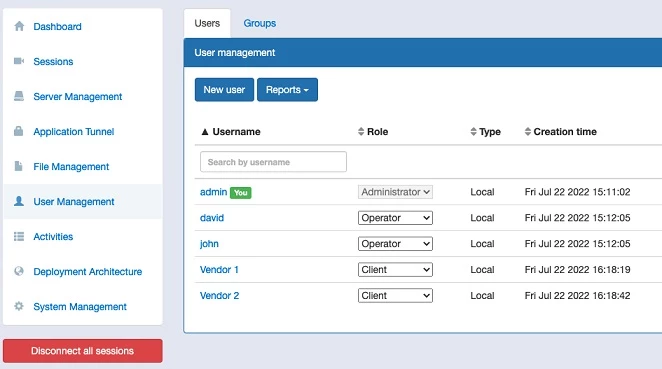
With SRA, IT teams can delegate administration of remote access to plant staff without worrying about compromising security or infrastructure. Since SRA uses a simple, static firewall configuration and secure application tunnel, it eliminates the need for ongoing network changes. New users can be provisioned by leveraging their existing identity provider in accordance with organizational security policies
Defining and enforcing granular access controls for industrial and government assets at multiple levels and geographic locations are essential for minimizing the risks to operations posed by internal and third-party remote users. SRA not only delivers these capabilities, but it also supports a Zero Trust security architecture and champions the least privilege principle.
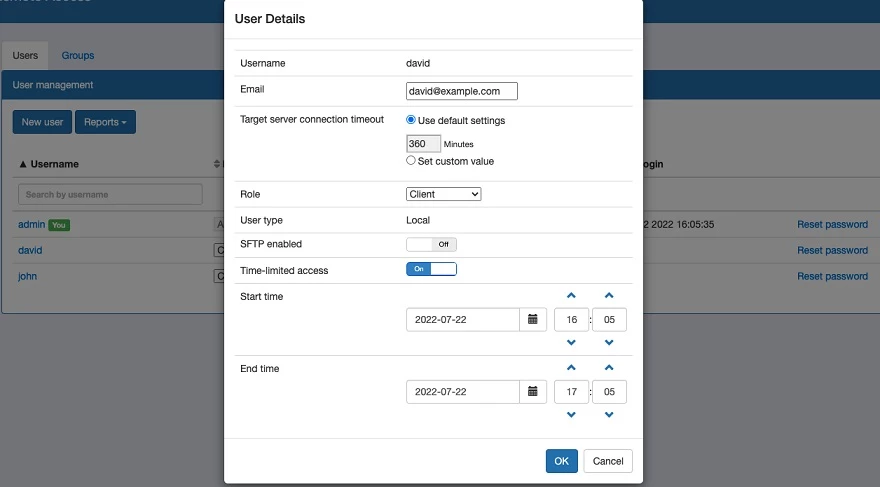
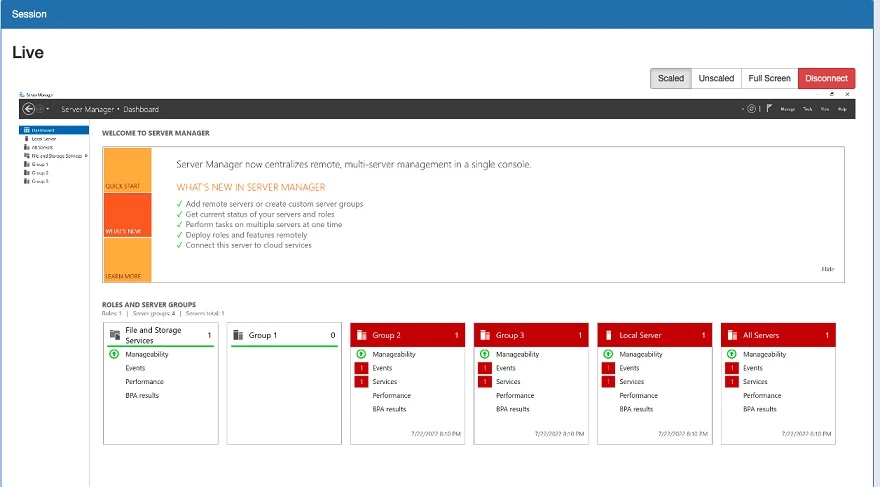
Traditional IT remote access tools only offer limited monitoring and auditing capabilities for remote user activity. SRA overs full visibility into user activity, giving the insights needed for optimal management. Administrators have the option to monitor active SRA sessions in real time for troubleshooting, user supervision, and emergency termination if necessary. In addition, SRA automatically records every session to support response actions, investigations, and training.
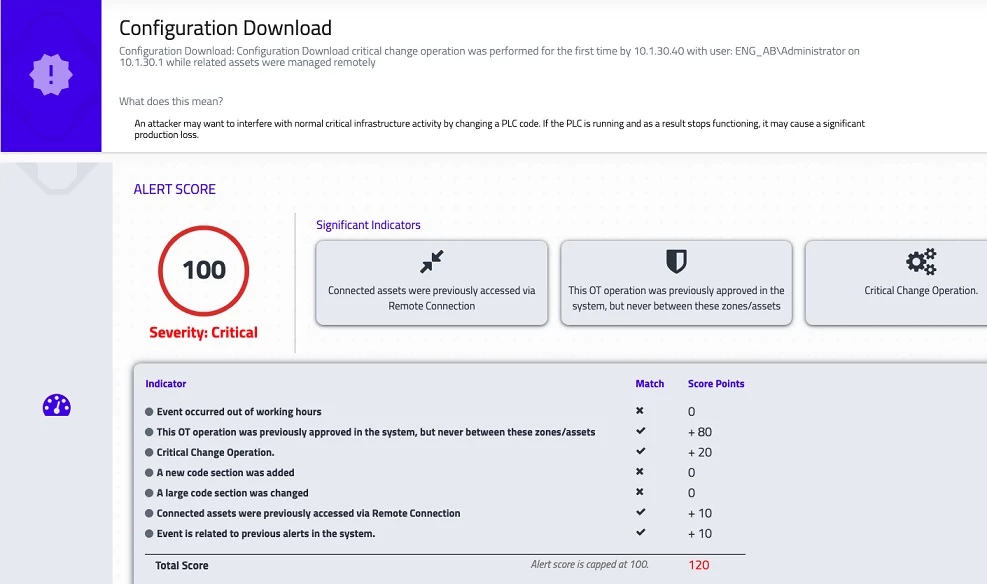
SRA integrates Claroty Continuous Threat Detection (CTD) to enable you to detect, investigate, and respond to cybersecurity incidents as they happen. CTD triggers an alert if a user engages in unauthorized activity, such as trying to service assets outside predetermined maintenance windows. From the alert, an administrator can go directly into the SRA session and monitor or disconnect.
Want the inside-scoop on how Claroty SRA will enable and secure your XIoT remote access use cases?




